How Would I Find Out if Someone Was Tracking an iPhone? 5 Signs!
is my phone being tracked
ALL TOPICS
- Phone Location Tracker
- Mobile Tracker Apps
- Mobile Tracker Tips
Dec 12, 2025 Filed to: Mobile Tracker Proven solutions
The monitoring software development has made it reasonably simple to keep an eye on Someone's mobile phone use. However, even if these surveillance technologies are intended for an employee or parental supervision, it is still conceivable that Someone may use them against you. Depending on the technology, the individual can see your email history, phone logs, text messages, account login information, and much more.
So, if you're wondering, "is my phone being tracked?" or how to know if someone is tracking your phone, here we will tell you 5 signs on how to tell if your phone is tracked and its countermeasure to protect yourself.
![]()
Try FamiSafe, Protect kids' online safety.
Table of Content
Part 1: How to know if someone is tracking my phone? 5 Signs!
Devices with monitoring or spy software put on them will act differently from untampered ones. The following are some indications that your actions are watched, your phone has been hacked or tracked by spy software:
1. Battery depletion more quickly: Spy software uses battery and device resources while active in the background. As a consequence, your device's battery will discharge more quickly as a result of this.
2. Unusual noises during calls: If you experience odd background sounds while talking, it's conceivable that someone is using a monitoring device to listen in on your calls. It is a symptom of a compromised phone.
3. The appliance is overheating: An app that updates data in the cloud would use many resources continuously, increasing the risk of the device overheating.
4. Increased use of data: The spy software will use many data since it transmits the device report to the monitoring person. You can notice this in the expanded data use on your smartphone. But remember that more than one indication is needed to guarantee anything. If all three of these symptoms coexist, you'll want to know how to handle the issue.

5. Abnormally asking for permission: Some applications may request unnecessary rights. For example, why is a note app requesting camera use permission? Why is a culinary app requesting permission to record voice? Keep this in mind when it occurs. If you have a pop-up camera on your phone—yes, they do exist—and it pops up without your intervention, that implies certain applications are covertly snapping pictures.
Part 2: How to Find for Spy Software on your Phone?
Unfortunately, hackers may easily get access to your phone. For them, it may be as easy as requiring you to click a link or install an app. It may be challenging to get the program off your phone after it's installation. Sometimes, you may not even be aware that it is there.
So, how can you find malware on an iPhone or an Android device? If you feel Someone is spying on you and you need to learn how to detect or track them, this section serves as a guide!
For iPhone:
Jailbreak: Apple does not allow the installation of spying or monitoring technologies. Because of this, if someone wants to put surveillance software on your phone, they must jailbreak it first. Jailbreaking entails eliminating the security constraints that Apple put in place for iOS. While jailbreaking an iPhone may improve access to iOS's fundamental features, it exposes your device to several security dangers.
- After jailbreaking the iPhone, installing surveillance software becomes pretty simple.
- Your iPhone's performance might have a negative impact by malware or other malicious applications that can quickly access its fundamental features.
- Your data and user accounts will be vulnerable to hackers.
- While attempting to jailbreak your iPhone, it may become unusable.
Install software from outside Apple's App Store: The Cydia software is installed when an iPhone is jailbroken, which might reveal the jailbreak. Because of this, if you discover the Cydia software on your iPhone and you didn't jailbreak your device, it implies someone else did it secretly and maliciously.
Accept invitations from find my iPhone without knowing: By default, you cannot tell the device is being seen with Find My iPhone. However, you can activate the System Service's status bar icon so that when any system service location tracking is enabled, the device displays the location services symbol in the status bar.
Using free/open/public WiFi spots: A public WiFi Internet connection implies that hackers can read your data since it does not need authentication. Additionally, the administrator of the WiFi network may be able to observe the websites you visit and may even sell your information.
For Android:
Rooted: The Android equivalent of eliminating OS limitations and gaining superuser access to the device's essential features is rooting an Android smartphone. But like jailbreaking, rooting Android comes with several security dangers.
- You would send updates to you over the air or OTA.
- Giving rogue programs root access will expose your data to risk.
- After rooting, rogue software may install certain more harmful applications without your awareness.
- Viruses and Trojans may attack your device.
Download virus: Malicious software called Stealthy Thief can trick Android smartphone users into believing their devices have been off. In reality, they are still active and vulnerable to misuse.

Part 3: How to use code to check if your phone is monitored?
Short codes can also be used to check if messages and data are secure and whether your phone is being monitored. This section provides code and instructions to secure smartphones against potential tracking.
*#21#
Using this code, you can check if calls, messages, and other data are being diverted. It will display the type of diversion and the number to which the information is diverted on your phone screen.
*#62#
If your calls, messages, and data appear to be diverted, use this code to identify the destination. It is likely that your voice calls have been directed to a number provided by your cellular provider.
##002#
To avoid the possibility of accrued charges due to auto-redirection, using a universal code to switch off all redirection settings on your phone is recommended before roaming.
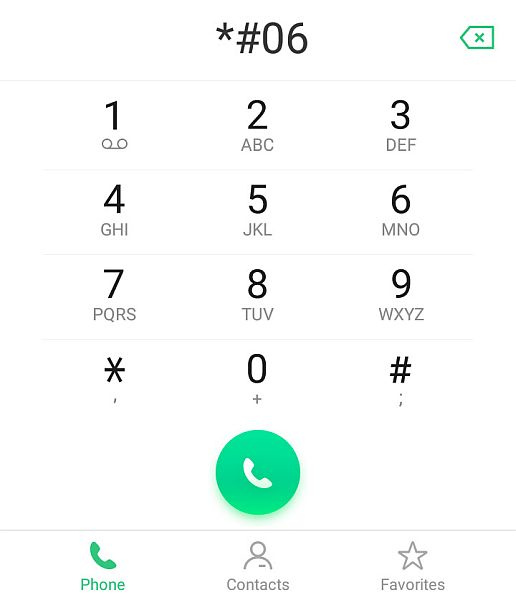
*#06#
This code can be used to determine your IMEI (International Mobile Equipment Identifier). Knowing this number can help you recover a lost or stolen phone, as its location is transmitted to the network operator even when a different SIM is inserted. Additionally, knowing someone else's IMEI number enables one to identify the model and technical characteristics of their phone.
Part 4: How to remove spy applications from your phone?
You may use the following methods to get rid of spy applications from your phone if you're wondering, "Is my phone being monitored using a spy app?" -
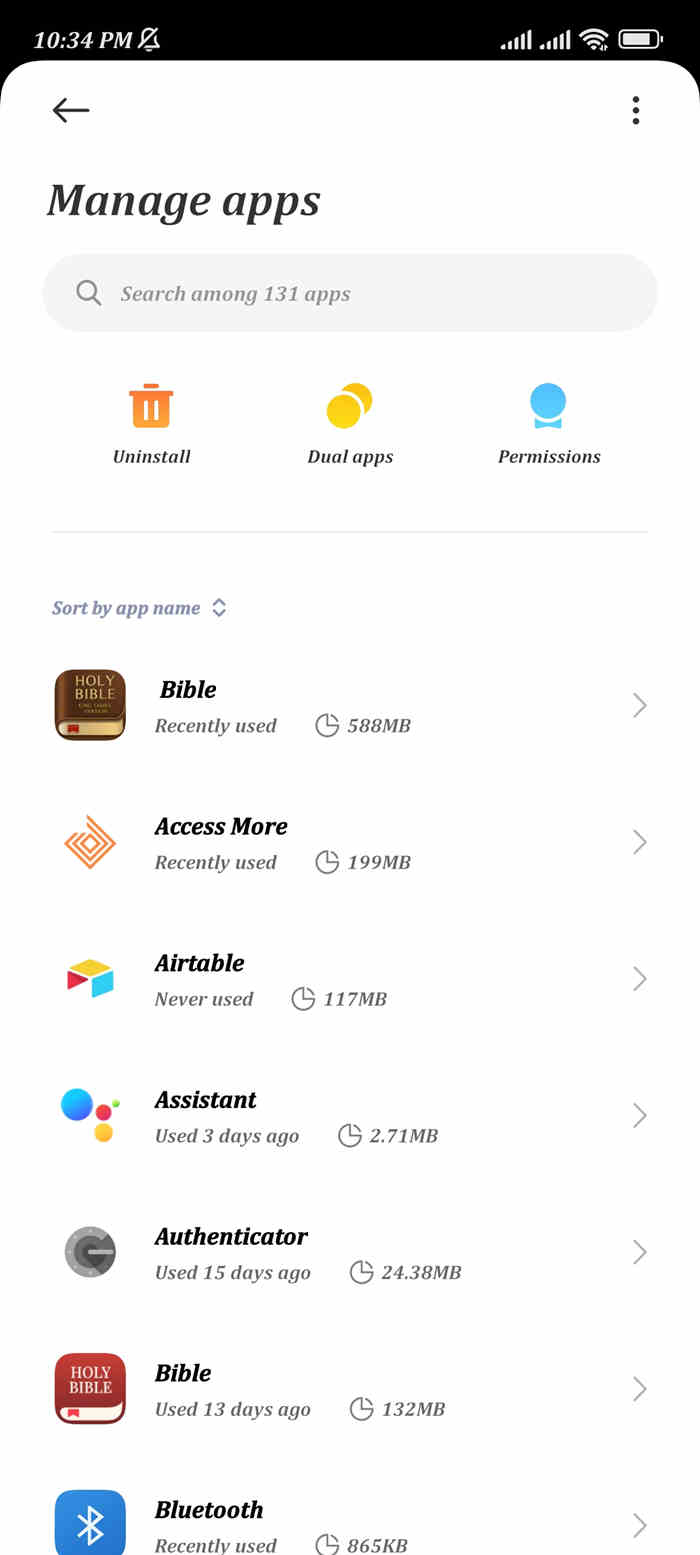
Delete manually from the Apps manager: Suppose you believe your smartphone is watched. In that case, tap the Apps Manager option in your device settings and manually uninstall the app since spy software will remove its icon and operate covertly in the background. No matter how sophisticated a spy program is or how hard it tries to conceal its existence, it will always be visible in Apps Manager, even if it pretends to be another crucial system function.
Update the OS on your device: Updating the operating system on your smartphone is another efficient way to get rid of a spy program. Like other software, spy applications rely substantially on OS compatibility to function. The surveillance software could not function correctly after updating your phone's OS, which would eliminate the danger. When you use iTunes to update the iOS on an iPhone, it will uninstall any apps you may have installed after jailbreaking the device.
Reset the factory settings: You may conduct a factory reset on your smartphone to get rid of the spy software if you can't discover it or if there has yet to be an OS upgrade published for your model. Your smartphone's factory reset will erase all the data and applications, including the Spy software. However, this approach should be the final one you attempt to remove the spyware since you will lose all the files on your device.

How can you safeguard your phone?
You must always maintain your phone security so that you won't need to be watchful of the symptoms that indicate someone installed a surveillance app.
Here's how to safeguard your phone from spy applications. -
Use a password to unlock the phone: If you keep your phone password-protected, they won't be able to install the spy program since every surveillance app requires physical access on the target device. It will shield your phone from unwanted access in addition to installing surveillance applications.
Don't jailbreak or root your phone: If you jailbreak or root your phone, malware may be able to install additional apps—including surveillance apps—without your knowledge. So, to prevent being watched, you install applications after rooting or jailbreaking your phone with great caution, or you don't.
Install an app for security: Utilising a security or antivirus program may reduce your device's vulnerability to malware or spyware installation. Any dangerous apps installed on your phone will be immediately detected and reported to you by these.
Update your device: Always maintain your device's OS and firmware up to date to address any security flaws in older software.
Avoid installing untrusted apps: You risk unintentionally downloading spyware or malware if you continue to install every other program you come across. Make sure an app is from a reputable developer before installing it.
Part 5: How to protect kids' cyber safety?
Kids are fascinated by applications from unknown sources. Therefore, they may download certain unsuitable apps when using their gadgets, unlike adults who may be concerned about the safety of these unverified programs. So, how can you tell whether your child's smartphone has downloaded an untrusted app? I endorse FamiSafe: Program Blocker as a strong and dependable parental control app. Have a quick look at this video to know how FamiSafe works:
You can quickly see which applications your kid has loaded or removed using this app's Software Blocker & Usage function. You will get notifications as soon as they install an untrusted app. Just prohibit any worthless applications. You may ban any program that is unsafe for your kid with this tool!
Thinking, "Is my phone being tracked?" may be frightful since you know that if your doubt is valid, then all your personal information on the phone might be at risk. The tracker might obtain your smartphone's user account information, contact list information, email, and other information.
This could expose your family to hazards along the road. Thus, we've provided you with some advice about "how to identify whether your Android is hacked." So, follow the tips above to delete the spy software from your phone after ensuring there has been no hacking.
- Web Filter & SafeSearch
- Screen Time Limit & Schedule
- Location Tracking & Driving Report
- App Blocker & App Activity Tracker
- YouTube History Monitor & Video Blocker
- Social Media Texts & Porn Images Alerts
- Works on Mac, Windows, Android, iOS, Kindle Fire, Chromebook



Thomas Jones
chief Editor